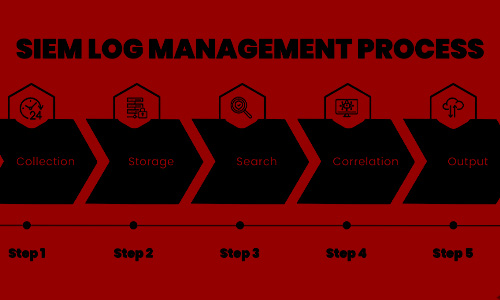
Log Management
SIEM acts as a centralized log management system, collecting and storing vast amounts of log data from diverse sources within the organization's network, including servers, applications, network devices, and security appliances.
Event Correlation
The system correlates data from multiple sources to identify patterns and relationships that may indicate security incidents. By connecting the dots between seemingly unrelated events, SIEM enhances the ability to detect complex and sophisticated threats.
Real-Time Monitoring
SIEM provides real-time monitoring of security events, enabling organizations to respond promptly to potential threats. This capability is crucial for identifying and mitigating security incidents before they escalate.
Incident Detection and Response
SIEM excel at detecting and alerting security teams to potential security incidents. Once an incident is identified, the system facilitates a coordinated and efficient response, minimizing the impact of the threat.
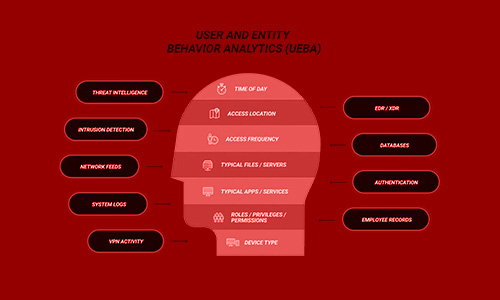
User and Entity Behavior Analytics (UEBA)
Allowing organizations to analyze and identify abnormal user behavior patterns. This helps in detecting insider threats, compromised accounts, and unauthorized access.
Compliance Management
Assist organizations in meeting regulatory compliance requirements by providing the necessary tools to monitor and report on security events. This is particularly valuable in industries with stringent data protection regulations.
Threat Intelligence Integration
Integration with threat intelligence feeds, enriching the analysis of security events with up-to-date information about known threats. This ensures that security teams can quickly identify and respond to emerging threats.
Dashboard and Reporting
Customizable dashboards and reporting features, providing security professionals and executives with a visual representation of the organization's security posture. This helps in making informed decisions and understanding the overall threat landscape.
Forensic Analysis
SIEM enables detailed forensic analysis of security incidents. Security teams can investigate the timeline of events, understand the root cause of incidents, and develop strategies to prevent similar occurrences in the future.
Automation and Orchestration
Automation and orchestration capabilities, allowing organizations to streamline incident response processes. Automated responses to certain types of incidents help reduce response times and mitigate potential damage.
Scalability
Scalability comes in the core of the SIEM, accommodating the growth of an organization's IT infrastructure. Whether it's an expansion of the network or an increase in data volume, a robust SIEM system can handle the demands of a dynamic digital environment
In conclusion, SIEM stands as a crucial component of a comprehensive cybersecurity strategy, offering a unified and intelligent approach to security event management. By providing real-time monitoring, incident detection, and a rich set of features, SIEM helps organizations stay resilient in the face of evolving cyber threats and maintain a proactive stance in safeguarding their digital assets.